Understand the types of Salesforce attacks you need to detect
Before you start combing through logs, define what you are looking for. “Salesforce attacks” typically fall into a handful of patterns, each leaving different traces:
- Phished admin or integration credentials: Attackers obtain a valid username/password or API key, then log in or call APIs from unusual IPs, countries, or at odd hours.
- OAuth token abuse via Connected Apps: A compromised integration or connected app grants wide read/write access, enabling data exfiltration at scale.
- Session hijacking: Stolen or replayed session tokens generate logins without MFA prompts, often visible as suspicious session origins or user-agent strings.
- Privilege escalation through configuration changes: New Permission Sets, altered Profiles, relaxed IP restrictions, or disabled MFA settings to maintain persistence.
- Data exfiltration via reports and exports: Massive report exports, Data Export runs, or programmatic bulk API pulls that don’t match normal patterns.
- Malicious automation: New or modified Flows, Apex, or Email-to-Case rules to quietly route data outward, create backdoor users, or notify attackers.
These behaviors leave artifacts across Login History, Setup Audit Trail, Event Monitoring, and various product-specific logs. The sections below walk you through exactly where and how to check.
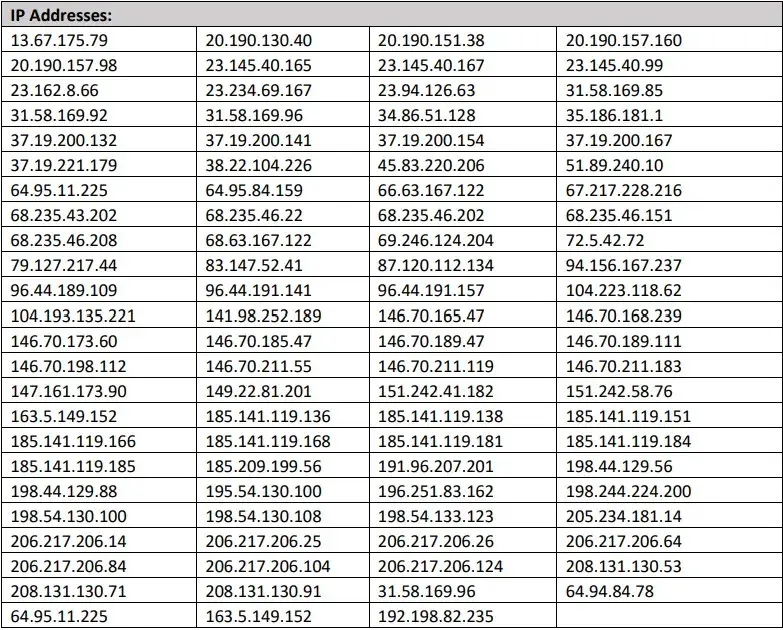
Ip's of the attackers are known
Refer to this list to check if any of these ip's has accessed your org.
Rapid triage checklist (first 30–60 minutes)
If you suspect an ongoing incident, start with high-signal indicators to quickly decide whether to escalate.
- Check Salesforce Trust for any platform-wide incidents that could explain anomalies. Use the Salesforce Trust Status page.
- Scan admin logins in the last 72 hours for unusual IPs, countries, or times. See Salesforce Help: View Login History.
- Review Setup Audit Trail for new users, permission changes, connected apps, or network access changes. See Salesforce Help: Setup Audit Trail.
- Identify integration users and check for traffic spikes, failed authentications, or API anomalies.
- Look for mass data events such as large report exports, Data Export runs, or unusual Bulk API activity.
- Freeze suspected users and revoke active sessions immediately if you see clear compromise. You can unfreeze later if it’s a false positive.
If two or more red flags appear together, shift into a deeper investigation and begin preserving evidence.
Core Salesforce logs and screens to review
Login History and Identity Verification
Navigate to Setup > Security > Login History. Export the last 7–30 days and sort by:
- Login status and failure reasons (e.g., invalid password, MFA challenge fails)
- Source IP, location, and user-agent—flag new countries, Tor/VPN patterns, headless browsers
- Unusual times for your team’s geography
Also check Identity Verification History (MFA challenges, device registrations). Multiple new device registrations for admins in a short period is suspicious. Reference Salesforce Help: Login and Verification History.
Active Sessions and Session Management
Go to Setup > Security > Session Management to view active sessions. Look for:
- Sessions from unexpected IP ranges or countries
- Long-lived sessions on admin accounts
- Multiple concurrent sessions for the same user from different geographies
If you suspect compromise, expire all sessions for affected users and force password resets.
Setup Audit Trail
The Setup Audit Trail records configuration changes. Pull the last 30–90 days and focus on:
- New users, role changes, and permission set assignments—especially for integration users
- Connected Apps created or updated, OAuth scopes changed
- Network Access or Session Settings changes (e.g., relaxed IP restrictions, disabled MFA)
- Remote Site Settings or Named Credentials added or altered
- Flows/Apex created or modified, Platform Events wired to external endpoints
Document any unexpected change with timestamps and the acting user.
Event Monitoring (Salesforce Shield)
If you have Shield Event Monitoring, pull event logs for the last 30 days (retention varies) for:
- LoginEvent and AuthSession: abnormal geographies, user-agents, failed MFA
- API and Bulk API: sudden volume spikes, off-hours pulls, new endpoints
- ReportExport and ListViewEvent: large exports or mass views
- LightningPageView anomalies indicating scripted browsing
- URI and RestApi events calling sensitive endpoints
Use the Event Monitoring Analytics app if available to visualize trends.
Reports, Dashboards, and Data Export
Data often leaves through sanctioned paths. Investigate:
- Recently Run Reports and Report Subscriptions for high-volume or sensitive objects (Leads, Opportunities, Cases, Contacts)
- Data Export (Setup) for unscheduled or unusual full exports
- Scheduled report emails to unfamiliar recipients or external domains
Correlate these events with user activity and IPs in Login History or Event Monitoring.
Product-specific checks beyond core CRM
Marketing Cloud (ExactTarget)
For Marketing Cloud, review:
- Audit Trail for user creation, role changes, and API user modifications
- API integrations in Installed Packages and their permissions/tokens
- SFTP logs for new IPs, mass downloads, or off-hours transfers
- Triggered sends and journeys altered to route data externally
Commerce Cloud (B2C)
In Commerce Cloud, use Log Center and review:
- OCAPI and SCAPI access patterns
- Account Manager user changes and 2FA status
- Job logs for unexpected data exports
Experience Cloud (Communities)
For Experience Cloud, verify:
- Guest user permissions are locked down and haven’t changed unexpectedly
- Login History patterns for community users
- Any new flows or pages that expose data
Connected Apps, OAuth tokens, and integrations
Attackers frequently exploit integrations because they often have broad, quiet access. Examine:
- Connected Apps: validate Scopes, IP relaxation, and Permitted Users settings. Remove any unfamiliar apps.
- OAuth tokens: revoke unused or suspicious tokens; reauthorize critical integrations.
- Named Credentials: confirm endpoints and authentication methods; rotate secrets if you suspect compromise.
- Remote Site Settings: flag newly added domains, especially if they look similar to trusted ones (typosquatting).
- Integration users: check last login, IP ranges, and profile/permission set changes.
Indicators of data exfiltration you can verify
Even if credentials were used legitimately, data theft leaves footprints. Review for:
- Spikes in API calls tied to objects like Contact, Lead, Account, Case, Opportunity
- Unusual bulk queries with high record counts
- Large ReportExport or DataExport events in Event Monitoring
- Automations that email spreadsheets externally or post to webhooks
- Analytics dataset exports or Einstein Discovery data extractions
Correlate the timing with user activity and any configuration changes to understand intent and scope.
Safety checks that help rule out false positives
Not every anomaly is an attack. Validate:
- Change windows: Did a scheduled deployment introduce expected changes?
- New integrations or pilots: Is a vendor or internal team testing a new connector?
- Corporate VPN changes: Did your networking team change egress IP ranges?
- User travel: Are unusual logins explained by legitimate travel?
When in doubt, confirm with system owners before escalating.
Containment steps if you find signs of compromise
Once indicators point to a likely breach, act quickly to contain without destroying evidence:
- Freeze affected users in Salesforce and expire sessions globally for those users.
- Revoke OAuth tokens and disconnect compromised Connected Apps.
- Reset passwords for compromised and high-risk users; enforce MFA immediately if not already required.
- Rotate integration secrets, API keys, and Named Credential auth details; re-issue certificates where applicable.
- Lock IP ranges temporarily to corporate networks where feasible.
- Snapshot and export logs (Login History, Setup Audit Trail, Event Monitoring) and preserve system state for investigation.
Use vendor references such as Salesforce Help: Security Best Practices and your internal incident response runbooks.
Evidence preservation and timelines
Salesforce log retention varies by edition, products, and licensing. To avoid losing critical data:
- Export Login History and Setup Audit Trail immediately.
- If you have Event Monitoring, export relevant event types for the full retention window.
- Capture configuration baselines (Profiles, Permission Sets, Connected Apps, Remote Site Settings) before making large changes.
- Record timestamps, user IDs, IPs, and any correlations across systems (IdP, email security, EDR, SIEM).
If you use a SIEM, pull parallel data (IdP MFA logs, firewall, proxy, endpoint) to validate findings.
Cross-check with identity and email systems
Many Salesforce compromises begin with identity attacks. Review:
- SSO/IdP logs for MFA bypass, impossible travel, and unusual risk scores
- Conditional Access or Login IP policy violations
- Email security logs for phishing related to Salesforce or integration brands
If your IdP is integrated with Salesforce, ensure enforcement of MFA and device trust. See Salesforce Help: SSO and SAML Configuration.
Benchmark against Salesforce Security Center and Health Check
Two native tools can highlight risky posture:
- Security Center: For multi-org oversight, surfaces weak controls and drift. See Salesforce Help: Security Center.
- Health Check: Compares org security settings to baselines. Focus on password policies, session security, MFA, and clickjack protection. See Salesforce Help: Health Check.
Use these to prioritize quick wins and reduce exposure during and after an incident.
What to tell stakeholders while you investigate
Clear, timely communication reduces panic and keeps teams aligned. Share:
- What’s known: timeline, affected features/users, attack indicators
- What’s unknown and being validated
- Immediate protections enacted (MFA enforcement, token revocations, IP lock-downs)
- Next update time and points of contact
Avoid technical jargon unless your audience requires it. Preserve evidence and avoid sweeping resets that erase audit trails prematurely.
How to compare and learn from similar checks in HubSpot
If your team also uses HubSpot or you’re mapping cross-CRM threats, mirror your checks. Helpful references:
- HubSpot Help Center: User activity logs—review logins, exports, and data deletions
- HubSpot Help Center: Export and audit—validate report and list exports
- HubSpot Security: Account protection—enable 2FA and monitor login notifications
Cross-platform anomalies (e.g., the same IP touching both CRMs) are strong signals of an identity-led campaign.
Hardening steps to prevent repeat incidents
Once immediate risk is contained, close the gaps that enabled the attack:
- Enforce MFA universally via Salesforce or IdP and block legacy auth where possible.
- Constrain admin accounts: separate admin users, require VPN/IP restrictions, and short session lifetimes.
- Right-size permissions: minimize “Modify All Data,” audit Permission Sets regularly.
- Harden Connected Apps: restrict to approved users, review OAuth scopes, require high-assurance sessions.
- Rotate secrets and certificates on a schedule and after any incident.
- Monitor continuously: export Event Monitoring logs to a SIEM, alert on spikes in API/ReportExport, and failed MFA storms.
- Phishing-resistant MFA: consider security keys or device-bound passkeys for admins.
- Change management discipline: require approvals for production config changes and log them centrally.
Step-by-step investigation workflow you can reuse
To structure your response, work through this repeatable flow:
- 1. Validate signals: triage logins, audit trail, and trust status.
- 2. Scope: identify affected users, apps, and data; map timelines.
- 3. Contain: freeze users, revoke tokens, rotate secrets, enforce MFA.
- 4. Collect evidence: export logs, snapshot config, gather SIEM and IdP records.
- 5. Eradicate: remove malicious changes, uninstall rogue integrations, patch misconfigurations.
- 6. Recover: restore known-good automations and validate data integrity.
- 7. Improve: update runbooks, close gaps, and train users.
Document findings and create detection rules for every root cause uncovered.
Common red flags worth escalating
Escalate when you see any of the following, especially in combination:
- New admin users or elevated permissions without a change ticket
- MFA disabled or session timeouts lengthened
- Connected Apps added, with broad OAuth scopes, from unfamiliar publishers
- Report exports or Bulk API pulls far above baseline
- Login spikes from unfamiliar countries or ISPs
- Flows or Apex that send data to new external endpoints
- Named Credentials pointing at lookalike domains
Correlate these with user communications and project schedules, but assume compromise until proven otherwise.
Where ASC Digital can help
If you need a second set of eyes or want to speed up containment, our specialists can assist with rapid audit, forensics, and hardening:
- ASC Digital can provide a structured review of controls, logs, and risky integrations
- Provide hands-on triage, scoping, and remediation
- Offer ongoing monitoring, patching, and configuration hygiene
- Optimize and reduce integration risk without losing flexibility
- ASC Digital Contact—reach our team 24/7 for urgent help
We also provide runbooks tailored to your Salesforce edition, industry, and regulatory environment.
Practical queries and patterns to use in your SIEM
If your Event Monitoring and IdP logs flow into a SIEM, create alerts for:
- Multiple failed MFA challenges followed by a success for the same user
- New Connected App with high-privilege scopes
- ReportExport volume spikes relative to 30-day baseline
- Bulk API request counts crossing thresholds per user per hour
- Logins from new countries for admin users
- Setup Audit Trail entries for Session Settings or Network Access changes
Even basic threshold alerts can radically reduce time-to-detect.
Training and process upgrades that pay off fast
Most incidents start with social engineering. Reinforce:
- Phishing simulations and just-in-time training targeted at admins and integration owners
- Privileged access workflows requiring approvals and short-lived elevation
- Vendor and app onboarding checklists to validate scopes, data access, and logging before go-live
- Playbooks that precisely outline how to freeze, revoke, export logs, and notify stakeholders
Keep your runbooks stored where on-call responders can reach them quickly.
Admin-friendly worksheet to confirm or rule out impact
Use this quick worksheet to decide if you were affected and what to do next:
- Login anomalies: Any suspicious admin logins? If yes, note user, IP, time.
- Audit changes: Any unexpected permission changes or connected apps added?
- Data movement: Any large report/data exports or Bulk API spikes?
- Integration review: Any tokens or secrets potentially exposed? Rotate.
- Containment: Have you frozen accounts, revoked sessions, and enforced MFA?
- Evidence: Have you exported relevant logs and captured baselines?
- Communication: Stakeholders notified, next update scheduled?
If you check two or more boxes with “yes,” treat the incident as impactful and continue scoping until proven otherwise.
When to call in specialist support
Escalate to internal security or external responders when:
- Data exposure of regulated information is possible (PII, PHI, PCI)
- Multiple systems show correlated compromise
- OAuth or SSO keys and certificates may be exposed
- You lack Event Monitoring visibility or in-house forensic expertise
Prompt, expert triage can reduce dwell time and regulatory impact.
Make your next investigation faster
Finally, invest a few hours now so the next suspected attack takes minutes to triage instead of days:
- Centralize logging: Stream Salesforce Event Monitoring and IdP logs to your SIEM.
- Pre-build dashboards for logins, API usage, and exports.
- Automate exports of Login History and Audit Trail on a schedule.
- Keep a contact roster for app owners, admins, and security responders.
- Run quarterly “attack drills” to verify everyone can execute the playbook.
The combination of clear visibility, crisp playbooks, and strong identity controls is your best defense against Salesforce-centered attacks.